HTTP vs HTTPS: Understand the differences
Table of Contents
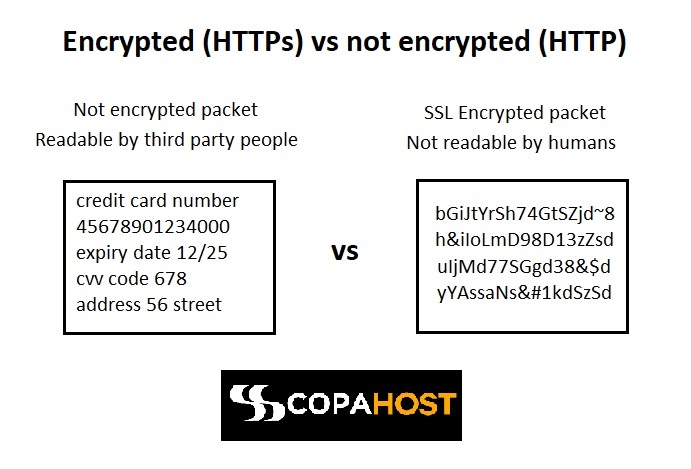
HTTP (Hypertext Transfer Protocol) and HTTPS (Hypertext Transfer Protocol Secure) are two protocols that transmit data over the internet. The primary difference between HTTP vs HTTPS lies in the level of security and encryption they provide.
HTTP operates on port 80 and sends data in plain text format. This means that the information transmitted between the client (such as a web browser) and the server is not encrypted. As a result, HTTP is susceptible to security threats, including eavesdropping, data interception, and manipulation. We recommend using HTTP for non-sensitive data or when security is not a major concern.
On the other hand, HTTPS operates on port 443 and ensures secure communication by encrypting the data. It uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols to establish an encrypted connection between the client and the server. This encryption ensures that the data exchanged remains confidential and cannot be easily intercepted or tampered with. Devices use HTTPS to transmit sensitive information, such as passwords, credit card details, and personal data, as it provides a higher level of security.
HTTPS requires the use of SSL/TLS certificates. Trusted certificate authorities issue such certificates. These certificates verify the authenticity of the server and establish a secure connection with the client. The presence of a valid SSL/TLS certificate indicates that the website or service is legitimate and helps users trust the security of their data.
In summary, while HTTP operates on port 80 and sends data in plain text, making it less secure, HTTPS operates on port 443 and encrypts the data, providing a higher level of security. Specialists recommend HTTPS for transmitting sensitive information over the internet, as it protects against eavesdropping, data interception, and tampering. The use of SSL/TLS certificates further enhances the security and trustworthiness of HTTPS connections.
What is Cryptography?
Cryptography refers to the process of converting ordinary plain text into a coded text. Applications do that to protect the information from any kind of theft or fraud. It involves storing and transmitting data in an encrypted form so that it can only be read and processed by the intended persons. When we compare HTTP vs HTTPS, it’s important to know about the cryptography.
Cryptography is the practice and study of techniques used for secure communication, data protection, and information integrity. It involves the use of mathematical algorithms and principles to transform plaintext (readable and understandable data) into ciphertext (encrypted and unintelligible data), making it difficult for unauthorized individuals to access or comprehend the original information.
The main objectives of cryptography are:
- Confidentiality: Ensuring that information remains private and can only be accessed by authorized parties. Encryption techniques are employed to protect the confidentiality of data.
- Integrity: Ensuring that information remains unaltered and tamper-proof during transmission or storage. Cryptographic mechanisms, such as digital signatures and hash functions, are used to verify the integrity of data.
- Authentication: Verifying the identity of users or entities involved in a communication or transaction. Cryptographic methods like public key infrastructure (PKI) and digital certificates are used for authentication purposes.
- Non-repudiation: Preventing the denial of involvement or the inability to refute a commitment or transaction. Cryptographic techniques, such as digital signatures, provide proof of the origin and integrity of data.
Cryptography employs various algorithms, encryption schemes, and cryptographic protocols to achieve these objectives. It encompasses symmetric encryption, asymmetric encryption (public key cryptography), hash functions, digital signatures, key exchange protocols, and more.
The field of cryptography is constantly evolving as researchers develop new algorithms and protocols to address emerging threats and advances in computational power. It plays a crucial role in securing sensitive data, online transactions, communication channels, and digital systems in various domains, including finance, e-commerce, cybersecurity, and government communications.
How an HTTPS server works
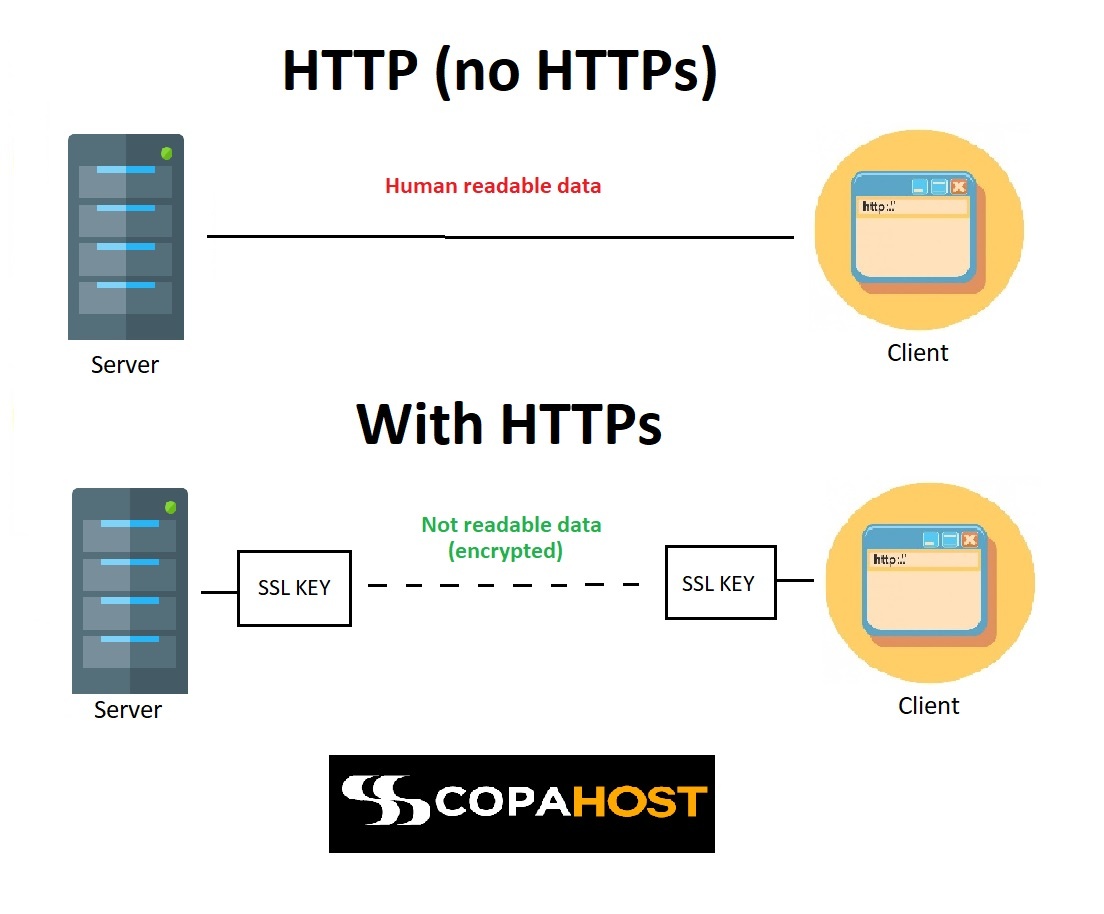
HTTPS is a secured version of the HTTP protocol. It establishes a secure communication link between the browser and server by encrypting the data. The HTTPS protocol pairs with TLS (transport layer security). It guarantees data privacy for the end-user. Considering the comparison of HTTP vs HTTPS, the HTTPS method is safest.
HTTPS server basically works according to the process of handshakes for setting up a secure connection.
Whenever your browser connects to the HTTPS server, the server acknowledges with its certificate. After this, the browser carries out a check for verifying the validity of the certificate. The certificate is valid only if:
- the owner information matches with the server credentials that the user requested for.
- the certificate is signed by a legitimate certification authority.
If any of these conditions fail, the user receives a warning about the problem.
The web servers perform several handshakes when HTTPS is active. Firstly, the initial step involves sending a request to the server for verification. If it is the desired one where information is destined to reach, it responds back by sending an acknowledgement message. Thus, after verification of authentic destination, the client sends a hello message. After this, information becomes encrypted and is exchanged via the use of encryption keys or cyphers.
The difference between HTTP vs HTTPs
HTTP is a set of protocols governing how any information can be transmitted on the World Wide Web. It defines a set of standard rules for web browsers & servers to communicate. It is an application layer protocol working on TCP/IP. It’s much riskier to intercept data transferred using HTTP rather than HTTPS. It happens because of the lack of data encryption. The HTTP server works over port 80.
Whereas, on the other hand, its extension and advanced version, HTTPS is fully secure. HTTPS works in conjunction with SSL/TLS protocols, thereby protecting the information from theft or changes. An HTTPS server works over port 443.
What is an SSL certificate?
Applications use SSL (Secure Sockets Layer) certificate, also known as Digital certificate, to establish secure and encrypted communication between a website and an internet browser. It works by creating a secure link between a website and a visitor’s browser. A few years ago, SSL certificates were only most common on a few websites. At that time, only sites where users provided personal data, credit card information or private data. Nowadays, the whole internet is changing. Most of the sites now have SSL certificates and works over HTTPS. Comparing HTTP vs HTTPS, the HTTP has no SSL certificate. So, HTTP is the non-secure method.
Security improvement between HTTP and HTTPS
The primary difference between HTTP and HTTPS lies in the security aspect rather than performance. HTTPS provides an additional layer of encryption and authentication through the use of SSL/TLS (Secure Sockets Layer/Transport Layer Security) protocols. This encryption ensures that data transmitted between a user’s browser and the website is secure and protected from potential eavesdropping or tampering.
HTTP vs HTTPS performance difference
In terms of performance, there can be a slight overhead when using HTTPS due to the encryption and decryption processes. However, with advancements in hardware and software optimizations, the performance impact of HTTPS has significantly decreased over the years. Modern web servers and browsers are designed to handle HTTPS efficiently, and the difference in performance between HTTP and HTTPS is often negligible for most websites.
HTTPS has lots of security benefits that outweigh the performance impact of using HTTPS. It helps protect sensitive information, such as login credentials, payment details, and user data, from interceptions. Also protects from malicious actors.
In recent years, there has been a push to encourage the widespread adoption of HTTPS for all websites, with major browsers displaying warnings for non-secure HTTP websites. This emphasis on security has made HTTPS the recommended standard for website communication, even for non-sensitive pages.
In summary, while there might be a slight performance difference between HTTP and HTTPS, the security advantages of HTTPS generally outweigh any negligible impact on performance. As a result, specialists highly recommended to use HTTPS for secure and encrypted communication between websites and users.
HTTP vs HTTPS Ports
HTTP and HTTPS are both communication protocols. Devices use them to transmit data over the internet. The main difference between them lies in the way data is encrypted and secured.
HTTP operates on port 80, while HTTPS operates on port 443. Ports identify specific services or processes on a computer or network. When a client, such as a web browser, communicates with a server, it connects to a specific port to establish a connection.
HTTP, operating on port 80, sends data in plain text format, which means the information transmitted between the client and the server is not encrypted. This lack of encryption makes HTTP vulnerable to security threats, such as eavesdropping or data manipulation. Therefore, HTTP is not suitable for transmitting sensitive information like passwords or credit card details.
On the other hand, HTTPS, operating on port 443, provides a secure and encrypted connection between the client and the server. It uses SSL (Secure Sockets Layer) or TLS (Transport Layer Security) protocols to encrypt the data during transmission. This encryption ensures that the data exchanged between the client and the server remains confidential and cannot be easily intercepted or tampered with by malicious actors.
In summary, the main difference between HTTP vs HTTPS is the level of security provided. HTTP does not encrypt the data, while HTTPS encrypts the data to ensure its confidentiality and integrity. When you transmit sensitive information or secure transactions, security specialists recommend using HTTPS.
TLS vs SSL
TLS (Transport Layer Security) and SSL (Secure Sockets Layer) are cryptographic protocols that provide secure communication over networks. While they serve a similar purpose, there are some key differences between TLS and SSL:
- Development and Versions: SSL was developed by Netscape in the 1990s and had multiple versions (SSL 1.0, SSL 2.0, SSL 3.0). TLS was introduced as an improved and more secure version of SSL and has its own versions (TLS 1.0, TLS 1.1, TLS 1.2, TLS 1.3).
- Security: TLS has stronger security features compared to SSL. It addressed several vulnerabilities found in SSL versions and introduced stronger encryption algorithms, hashing algorithms, and key exchange methods. TLS 1.3 is the latest version and provides significant improvements in security and performance.
- Handshake Process: The handshake process in TLS and SSL differs. In SSL, the handshake involves a series of messages exchanged between the client and server to negotiate the encryption algorithms, authenticate the server, and establish the session keys. TLS follows a similar handshake process but includes additional security features such as forward secrecy, where session keys are generated for each session and are not stored, making it more resilient against future key compromises.
Also…
- Cipher Suites: SSL and TLS support different cipher suites, which are combinations of encryption algorithms, hashing algorithms, and key exchange methods. TLS cipher suites are more secure and robust, supporting stronger encryption algorithms like AES (Advanced Encryption Standard) and more secure hash functions like SHA-256.
- Interoperability: TLS and SSL are not directly compatible with each other due to protocol differences. TLS supports backward compatibility with SSL, allowing a TLS-enabled server to accept SSL connections for compatibility purposes. However, it is recommended to use TLS for security reasons.
- Industry Adoption: Due to the security vulnerabilities found in SSL, industry-wide adoption has shifted towards TLS. Most modern web browsers and servers prioritize TLS, and SSL is considered outdated and insecure.
In summary, TLS is an improved and more secure version of SSL. It offers stronger security features, improved cipher suites, and a more robust handshake process. Providers widely adopt and recommend TLS for secure communication over networks. Specialists consider SSL outdated and less secure.
HTTPS and SEO on Google
It’s a tendency to have all the internet running over secure servers. Within the Google algorithm update on April 16th of 2017, Google is valuing much more HTTPS sites nowadays. In other words, it’s very difficult to get good rankings with an HTTP website.
In version 68 of Google Chrome, it warns as risky all the non-secure websites and shows a broken lock icon to the customers. If you compare HTTP vs HTTPS, Google will prioritize HTTPS secure websites.
HTTPS is an essential element for SEO (Search Engine Optimization) due to its role in enhancing website security. By encrypting the communication between a user’s browser and a website, HTTPS ensures that sensitive information remains private and cannot be accessed or tampered with by malicious parties. Search engines prioritize user safety, and they reward websites that prioritize security by implementing HTTPS. They will give better search rankings to safe websites.
Trust and credibility are crucial factors in SEO, and HTTPS plays a significant role in building them. When users see the padlock symbol and “https://” in their browser’s address bar, they know that the website they are visiting has taken measures to secure their data. This secure browsing experience fosters trust on the website, encouraging users to engage with the content, make purchases, or provide personal information. Search engines aim to deliver reliable and trustworthy results, so they give preference to websites that prioritize user trust by implementing HTTPS.
Security matters for Google
The adoption of HTTPS can have a positive impact on a website’s search engine rankings. While HTTPS is not the most significant ranking factor, Google considers it a ranking signal. Websites that use HTTPS are more likely to receive a slight boost in search engine rankings compared to their non-secure counterparts. Search engines prioritize delivering the best user experience, and secure websites contribute to that goal. Therefore, implementing HTTPS can help improve a website’s visibility in search engine results.
HTTPS preserves referral data, which is crucial for tracking the sources of website traffic. When the web server directs traffic from an HTTPS website to a non-HTTPS website, the referral isn’t usually present. Browsers and servers usually report this traffic as “direct.”
However, in HTTPS, servers will preserve referral data. That allows website owners to accurately track the sources of their traffic. This information is valuable for understanding the effectiveness of marketing campaigns, optimizing website performance, and making informed decisions to improve SEO strategies. By adopting HTTPS, website owners ensure they have access to accurate referral data and can effectively analyze and optimize their traffic sources.
What kinds of cryptography are available and their differences
There are several types of cryptographic algorithms and techniques available, each with its own characteristics and use cases. Here are some of the main categories of cryptography:
- Symmetric Encryption: Also known as secret-key or shared-key encryption, symmetric encryption uses a single shared secret key for both encryption and decryption. The same key is used to both scramble (encrypt) the plaintext into ciphertext and unscramble (decrypt) the ciphertext back into plaintext. Common symmetric encryption algorithms include Advanced Encryption Standard (AES), Data Encryption Standard (DES), and Triple DES (3DES).
- Asymmetric Encryption: Also called public-key cryptography, asymmetric encryption employs a pair of mathematically related keys: a public key for encryption and a private key for decryption. The public key can be openly shared, while the private key is kept secret. Data encrypted with the public key can only be decrypted using the corresponding private key. Asymmetric encryption is used for secure key exchange, digital signatures, and establishing secure communication channels. Popular asymmetric encryption algorithms include RSA, Elliptic Curve Cryptography (ECC), and Diffie-Hellman key exchange.
Despite the encryption, these are also important
- Hash Functions: Hash functions take input data and produce a fixed-size output called a hash value or digest. Hash functions are primarily used for data integrity verification and creating digital fingerprints of data. A small change in the input data should produce a significantly different hash value. Common hash functions include Secure Hash Algorithm (SHA-2 and SHA-3) and Message Digest Algorithm (MD5).
- Digital Signatures: Digital signatures provide authentication and non-repudiation by using asymmetric encryption. A digital signature is created by encrypting a hash value of the data using the signer’s private key. The recipient can verify the signature by decrypting it with the signer’s public key and comparing it with the computed hash of the received data. This ensures that the data has not been tampered with and came from the expected sender.
- Key Exchange Protocols: Key exchange protocols, such as Diffie-Hellman (DH), allow two parties to securely establish a shared secret key over an insecure communication channel. These protocols enable secure communication between parties who have never shared a secret key before.
It’s worth noting that cryptography also includes other areas such as cryptographic protocols (e.g., SSL/TLS), symmetric authentication codes (e.g., HMAC), and more.
Different cryptographic techniques serve different purposes and have varying levels of security, computational requirements, and scalability. To choose a cryptography, you must consider factors like the level of security, performance constraints, application requirements. You should also consider the threat model to address.
Advantages and disadvantages of HTTP and HTTPS
Advantages of HTTPS over HTTP:
- Data security and privacy
- Google loves HTTPS and will rank it higher
- Nowadays, there are cheap web hosting plans with free SSL certificates available.
Advantages of HTTP over HTTPS:
- It’s a cheaper protocol, as you don’t need to invest in certificates.
- It’s slightly faster, as it transfers fewer bits.
- Easier to configure at home, on a domestic server, for example.
Vulnerabilities
Both HTTP and HTTPS have their own vulnerabilities. As HTTPS has an extra encryption layer, it’s more secure. Here are some vulnerabilities of each protocol:
HTTP Vulnerabilities:
- Lack of Encryption: HTTP transmits data in plain text, making it vulnerable to interception and eavesdropping. Attackers can easily capture sensitive information, such as passwords or credit card details, while it’s being transmitted.
- Man-in-the-Middle Attacks: Attackers can intercept the communication between the client and the server by placing themselves between them. They can alter or steal data without the knowledge of the parties involved.
- Tampering: As data is transmitted in plain text, attackers can modify the content of HTTP requests or responses. This can lead to unauthorized access, data manipulation, or injection of malicious code.
HTTPS Vulnerabilities:
- Certificate Issues: HTTPS relies on digital certificates to establish trust between the client and the server. If a certificate is compromised, forged, or issued by an untrusted authority, it can lead to security breaches or man-in-the-middle attacks.
- Weak Cipher Suites: The strength of encryption algorithms and cipher suites used in HTTPS can vary. If weak or deprecated algorithms are employed, they may be susceptible to attacks like brute force or decryption.
- Malware and Phishing: While HTTPS protects data during transmission, it doesn’t guarantee the legitimacy of the website itself. Attackers can still use HTTPS to distribute malware or conduct phishing attacks by creating fraudulent websites with valid SSL certificates.
- Server Vulnerabilities: HTTPS doesn’t mitigate vulnerabilities at the server level. If the server hosting the website has security flaws, such as unpatched software or misconfigurations, attackers can exploit those vulnerabilities to gain unauthorized access.
It’s important to note that HTTPS addresses many of the vulnerabilities present in HTTP by encrypting data and providing integrity checks. It’s the recommended protocol for secure communication on the web.
Conclusion
The difference between HTTP vs HTTPS only happens in server-side communication. There is no change in the URL and the domain names.